Cyber security a public good

According to the prevailing security inequities and technology advancements, personal and corporate privacy has continuously eroded as cyber-attacks and data breaches become a daily issue to zero down with. In the first half of 2019 alone, more than 4.1 billion data records were exposed in known data breaches. The average cost of data breaches for affected companies is now nearly $4 million per business.
Standing guard while our society becomes ever more dependent on technology is the $120 billion cybersecurity industry, which is expected to grow to $300-plus billion by 2024. With the coming ages of AI and IoT, we stand to benefit from having an internet-connected home, vehicle or daily schedule to further automate and organize our lives.
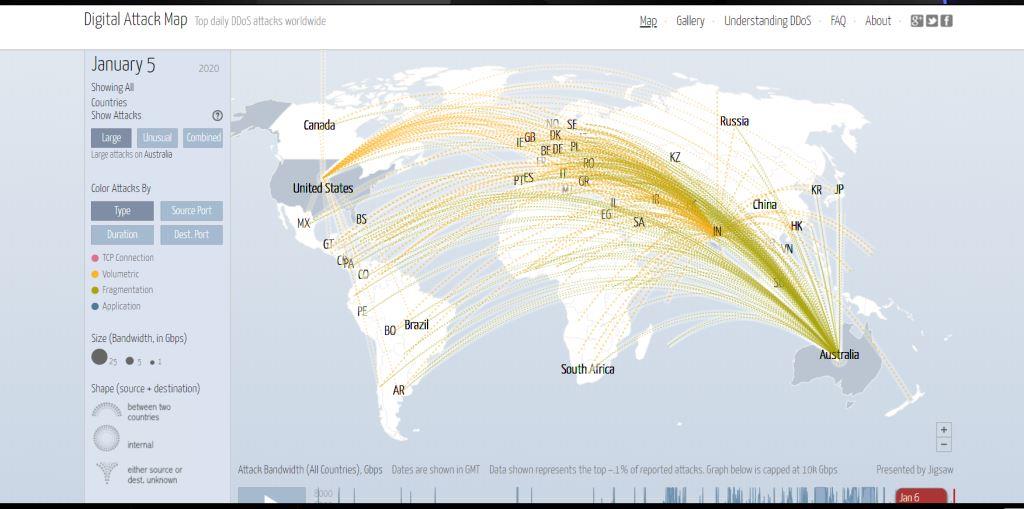
The question arises from the analysis: What would be the impact of being connected to the internet in great numbers? According to the live online threat forecast where cyber-attacks are occurring in a minimum duration of seconds, it’s therefore imperative that companies have the necessary security measures to survive as a formidable business.
What is happening in the cyber-world today?
Looking at the analysis of technology today, it does not surprise that soon your fridge will be able to buy your fruits on Amazon using your credit card credentials from its data set and having noticed what you liked on Facebook and Instagram.
Cyber security is crucial for this to happen; to make sure that, while our food preferences are being noted, our identity is not stolen, credit cards not cloned, and our devices not tampered with by threat actors that steal data or modify our device’s behavior.
As the Fourth Industrial Revolution takes progress and the integration and interaction of technologies in our social life so that individual standards are improved and environmental well-being, it is mandatory that cybersecurity will be ever more important.
In 2015, the UN identified 17 Sustainable Development Goals (SDGs) to be achieved by 2030 – ranging from eradicating poverty and guaranteeing stability and peace to fighting discrimination and climate change. Digital technologies, particularly the internet of things (IoT) and artificial intelligence (AI), can facilitate efforts to achieve the SDGs. For example, AI can help detect malnutrition using photographs of individuals living in a given area. Here, too, cybersecurity is crucial. Should pictures of those individuals be stolen or the AI model become corrupted, the use of AI to fight starvation would become problematic. Cyber security underpins trust in, and thus the adoption of, digital technologies for humanitarian and environmental purposes.
The lack of effective cybersecurity measures has a potential knock-on effect on the Fourth Industrial Revolution, and the development of information societies around the globe. Two aspects are particularly relevant: stability and trust. Without effective security measures in place, cyber-threats may undermine the stability of information societies, making digital technologies a source of risk more than a source of development. At the same time, a lack of security around digital technologies will erode users’ trust, which will in turn cripple adoption and hinder innovation. Cyber security is an essential resource of information societies and improving it is vital to fostering societal development, technological progress, and harnessing the potential of digital technologies to deliver outcomes that are beneficial to society.
Which cybersecurity?
The term cybersecurity covers a vast domain. It ranges from designing robust systems that withstand cyber-attacks, to coming up with methods and systems for threat and anomaly detection (TAD), guaranteeing systems’ resilience and defining systems’ responses to attacks.
Societies that use digital infrastructure to function, systems’ robustness is an essential requirement. But system hardening is a costly process. Requires accurate design, code verification and validation, testing and probing for vulnerabilities. This makes cybersecurity a club good – namely, a good that is not exhausted by its use but whose access is regulated by its cost.
Escalation of cyber-threats is a sign that this approach is ineffective, if not problematic, because market dynamics and the costs associated with improving systems’ robustness lead to an uneven distribution of cybersecurity measures.
Consider, for example, the IoT. The robustness of digital end-point devices has an impact on their costs, to the extent that producers may sacrifice robustness in the interest of retaining commercial competitiveness.
In 2018, a Symantec study reported an average of 5,200 attacks per month on IoT devices. As IoT increasingly pervades our private and public environments, its vulnerabilities may favor severe security and safety from threats. The question, then, is how do we develop and regulate the design of robust systems in an effective way?
Engineering robust systems has both a direct and indirect impact on the public in information societies. It enables critical national infrastructures and services to work, allows citizens to perform their daily routines, and can favor the socially beneficial outcomes of digital technologies. For these reasons, cybersecurity should not be framed and managed as a club good – it should be treated as a public good, which means no user can prevent others from using it.
Make cybersecurity a public good
Managing costs is key to developing systems’ robustness as a public good. This does not mean that systems’ robustness needs to come free of charge, but the costs mustn’t become a deciding factor in determining access. The key point here is to ensure that all users have access to digital technologies whose robustness is adequate to the purpose and the context of deployment.
This point can be clarified using two analogies: streetlights and national defense. These are two typical public goods; both come at a cost, but all citizens of a state access them independently of these costs, and they all contribute to maintain these goods by paying taxes. In the same way, cybersecurity can function as a public good if its costs are shared equitably among the relevant stakeholders. One implication of this approach is that the public sector will have to shoulder some of the costs of cybersecurity: this may include, for example, costs related to the setting of standards and certification procedures, as well as costs associated with testing and verifying technologies. But managing cybersecurity as a public good would also yield three important advantages: systemic approaches to security, shared responsibilities among the different stakeholders, and fostering collaboration.






Responses